2024-02-29 作者: Fisherworks
Take a look at this if your innobackupex insists on eating up most (or all) of your root partition, as playing hide and seek with you especially.
近两天总收到奇怪的推送,磁盘占用超90%,没采取人为任何措施,又自动降至正常……就很离谱。去翻了一下云监控的磁盘使用率,发现居然是系统盘,而非数据盘(后者占用率不高,多日无明显变化),就更奇怪了。
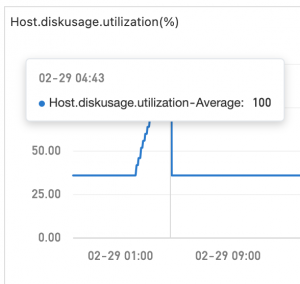
前者么,不逮住问题发生时的话,根本无从查起;考虑其发生规律,基本跟mysql冷备的时间周期比较吻合。
所以先去看mysql冷备文件的状态,就开始出问题了(截图欠奉)。
- 每个备份文件的结束时间都很早,从以往常见的上午9~10点提前到了凌晨4~5点。
- 且文件的大小也不太对劲,降了一半不止(在未删除数据的前提下)。
好办,备份文件会定期rotate但log不会,不删就会一直存,看log就好。
一看不要紧,近两天备份都是失败告终。
|
|
.......... 240209 05:05:01 >> log scanned up to (58627078203151) 240209 05:05:03 >> log scanned up to (58627086878169) innobackupex: Error writing file '/tmp/xbtempPr6mT8' (Errcode: 28 - No space left on device) xtrabackup: Error: write to logfile failed xtrabackup: Error: xtrabackup_copy_logfile() failed. |
这里的
/tmp 就很迷,我印象中所有临时文件都不应该去系统默认的temp目录,索性检查一下。
完整阅读本篇»






 京公网安备 11011502004657号
京公网安备 11011502004657号